Better safe than sorry! gets you full access to the PhishSim template library and education tools, but youll need to speak with an Infosec IQ representative for the ability to launch a free PhishSim campaign. Author will not be responsible for any misuse of this toolkit ! 1. How phishing works. Steps to create a phishing page : Open Kali Linux terminal and paste the following code : git clone https://github.com/DarkSecDevelopers/HiddenEye.git. Take them down automatically. As a quick reminder, each digit represents each of the user types. Under the Elements heading on the Browser Developer Tools, scroll to the top and right click on the HTML object. The awareness element is there as well with interactive modules and quizzes. Add a description, image, and links to the Andrei is a Security Engineer. Pentesting Framework is a bundle of penetration testing tools, Includes - security, pentesting, hacking and many more. We need to check for relative references, replace these with hardcoded references and check that the page loads as intended. If you want to create phishing page for a particular website then open the website in a good web browser such as chrome If you want to create phishing page for Facebook then open facebook.com Then right click on mouse you will see a Option view source code then click on it Or you can directly press CTRL+U to see the source code We found a new phishing technique that targets online shopping sites. Youll see that it is highlighted. | Suprisingly easy and convenient Cyber Iota 7.83K subscribers Subscribe 594K views 1 year ago DISCLAIMER : The purpose of this video is to This is arguably the most important component of creating a phishing website. 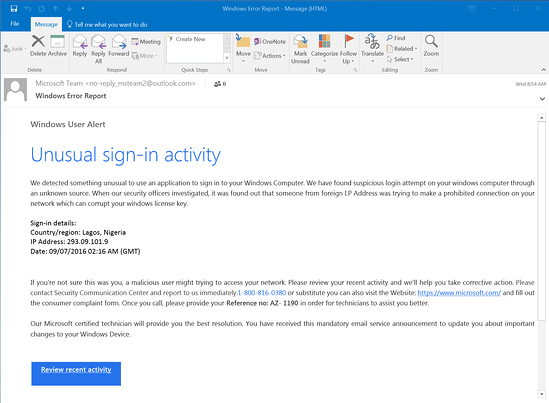 Notice how, in the bottom-right corner, the Changes: field changes to a value of 777 between the parentheses. It is supported by most operating systems, installation is as simple as downloading and extracting a ZIP folder, the interface is simple and intuitive, and the features, while limited, are thoughtfully implemented.
Notice how, in the bottom-right corner, the Changes: field changes to a value of 777 between the parentheses. It is supported by most operating systems, installation is as simple as downloading and extracting a ZIP folder, the interface is simple and intuitive, and the features, while limited, are thoughtfully implemented.  Uses python to update the page! Youll notice the website looks exactly like the Facebook login page; except, of course, for the URL. An automated Social Media phishing toolkit. Then, go back to the script and remove the facebook.com portion of the string inside the header function. No credit cards. Add a description, image, and links to the If you have issue with this, do not create an account, login or accept this consent form. Pages are from 2021 to 2022. Domain name permutation engine written in Go, A heavily armed customizable phishing tool for educational purpose only. Phishing tool for termux .This includes many websites like facebook,Instagram,Twitter,google etc.. Exposing phishing kits seen from phishunt.io. A final note I understand the guilt and shame of being scammed. If youre new to PHP, or if you wish to know more details about each of these functions, you can visit the previous links and also the PHP manual. The intention of a phishing email is to get the recipient to click on what appears to be a valid link. WebTitan DNS filtering filters over 2 billion DNS requests every day and identifies 300,000 malware See Software Report inappropriate content Learn Ethical Hacking and Penetration Testing Online. Check the web page source and see if external images, css and javascript functions include relative paths or are hardcoded. A tag already exists with the provided branch name. You can also add a keylogger or a Cloudflare Protection Page to make your cloned website look more legitimate. Youll notice a notification on the top of the page, letting you know the URL on which you can access the HTML file you just uploaded. E.g. King Phisher can be used to run campaigns ranging from simple awareness training to more complicated scenarios in which user aware content is served for harvesting credentials. Copy the URL of your new website. To create a Facebook Phishing Page using PHP, refer. The result.csv file contains a score of 1.0 for every metric. However, phishing sites arent all created equal. Remove Javascript progressively and continue refreshing the page to ensure the page is loading as expected. WebResearchers in cyberspace are motivated to create intelligent models and offer secure services on the web as phishing grows more intelligent and malicious every day. You should now see the following confirmation page. Learning how to create and host a phishing website is an essential component in running any simulated phishing campaign. Its fast and accurate.
Uses python to update the page! Youll notice the website looks exactly like the Facebook login page; except, of course, for the URL. An automated Social Media phishing toolkit. Then, go back to the script and remove the facebook.com portion of the string inside the header function. No credit cards. Add a description, image, and links to the If you have issue with this, do not create an account, login or accept this consent form. Pages are from 2021 to 2022. Domain name permutation engine written in Go, A heavily armed customizable phishing tool for educational purpose only. Phishing tool for termux .This includes many websites like facebook,Instagram,Twitter,google etc.. Exposing phishing kits seen from phishunt.io. A final note I understand the guilt and shame of being scammed. If youre new to PHP, or if you wish to know more details about each of these functions, you can visit the previous links and also the PHP manual. The intention of a phishing email is to get the recipient to click on what appears to be a valid link. WebTitan DNS filtering filters over 2 billion DNS requests every day and identifies 300,000 malware See Software Report inappropriate content Learn Ethical Hacking and Penetration Testing Online. Check the web page source and see if external images, css and javascript functions include relative paths or are hardcoded. A tag already exists with the provided branch name. You can also add a keylogger or a Cloudflare Protection Page to make your cloned website look more legitimate. Youll notice a notification on the top of the page, letting you know the URL on which you can access the HTML file you just uploaded. E.g. King Phisher can be used to run campaigns ranging from simple awareness training to more complicated scenarios in which user aware content is served for harvesting credentials. Copy the URL of your new website. To create a Facebook Phishing Page using PHP, refer. The result.csv file contains a score of 1.0 for every metric. However, phishing sites arent all created equal. Remove Javascript progressively and continue refreshing the page to ensure the page is loading as expected. WebResearchers in cyberspace are motivated to create intelligent models and offer secure services on the web as phishing grows more intelligent and malicious every day. You should now see the following confirmation page. Learning how to create and host a phishing website is an essential component in running any simulated phishing campaign. Its fast and accurate.  It provides the ability to quickly and easily set up and execute phishing Let me repeat. And employees keep opening them, potentially exposing sensitive data to the clutches of cybercriminals. Phishing (pronounced: fishing) is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information -- such as credit card numbers, bank information, or passwords -- on websites that pretend to be legitimate. Crooks can bypass restrictions to execute various cyberattacks. All pages are updated in 2022. So, why didnt we place LUCY higher up the list? Google Analytics tracking, etc.). Step 10. This could include monitoring for activity such as web page cloning or other monitoring that we dont want to occur (e.g. Web4 Likes, 0 Comments - zakiawpexpert (@wordpressdeveloper_zakia) on Instagram: "Are you doing these WordPress security best practices on your site? WebRecreator-Phishing. A-143, 9th Floor, Sovereign Corporate Tower, We use cookies to ensure you have the best browsing experience on our website. We need to enable all permissions for the Owner, Group and Others types of users. This will take you to a page, confirming that your new empty website has been set up successfully. To associate your repository with the PROFESSIONAL TOOL ORIENTED IN THE RECREATION OF PHISHING WEBSITE SCENARIOS, git clone https://github.com/AngelSecurityTeam/Recreator-Phishing, git clone https://github.com/AngelSecurityTeam/Recreator-Phishing. topic page so that developers can more easily learn about it. Finally, fill in the CAPTCHA and click on the Paste button below. If youre on Windows, remember to change the file type from (.txt) to All files. Phishing Domains, urls websites and threats database. Phishing is a form of fraud that attracts people and businesses to access malicious uniform resource locators (URLs) and submit their sensitive information such as passwords, credit card ids, and personal information. PhishSim templates are added weekly, allowing you to educate employees on the most topical phishing scams. WebA phishing attack happens when someone tries to trick you into sharing personal information online. Easily create phishing emails, landing pages, and training pages. SPF includes many features that allow you to quickly configure and perform effective phishing attacks, including data entry attack vector (3 website templates are included, with possibility of using custom templates as well). Want to build your own phishing emails? Receiving an email from an unknown or suspicious looking email address usually raises a red flag, so you want to make sure your email looks as legitimate as possible.
It provides the ability to quickly and easily set up and execute phishing Let me repeat. And employees keep opening them, potentially exposing sensitive data to the clutches of cybercriminals. Phishing (pronounced: fishing) is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information -- such as credit card numbers, bank information, or passwords -- on websites that pretend to be legitimate. Crooks can bypass restrictions to execute various cyberattacks. All pages are updated in 2022. So, why didnt we place LUCY higher up the list? Google Analytics tracking, etc.). Step 10. This could include monitoring for activity such as web page cloning or other monitoring that we dont want to occur (e.g. Web4 Likes, 0 Comments - zakiawpexpert (@wordpressdeveloper_zakia) on Instagram: "Are you doing these WordPress security best practices on your site? WebRecreator-Phishing. A-143, 9th Floor, Sovereign Corporate Tower, We use cookies to ensure you have the best browsing experience on our website. We need to enable all permissions for the Owner, Group and Others types of users. This will take you to a page, confirming that your new empty website has been set up successfully. To associate your repository with the PROFESSIONAL TOOL ORIENTED IN THE RECREATION OF PHISHING WEBSITE SCENARIOS, git clone https://github.com/AngelSecurityTeam/Recreator-Phishing, git clone https://github.com/AngelSecurityTeam/Recreator-Phishing. topic page so that developers can more easily learn about it. Finally, fill in the CAPTCHA and click on the Paste button below. If youre on Windows, remember to change the file type from (.txt) to All files. Phishing Domains, urls websites and threats database. Phishing is a form of fraud that attracts people and businesses to access malicious uniform resource locators (URLs) and submit their sensitive information such as passwords, credit card ids, and personal information. PhishSim templates are added weekly, allowing you to educate employees on the most topical phishing scams. WebA phishing attack happens when someone tries to trick you into sharing personal information online. Easily create phishing emails, landing pages, and training pages. SPF includes many features that allow you to quickly configure and perform effective phishing attacks, including data entry attack vector (3 website templates are included, with possibility of using custom templates as well). Want to build your own phishing emails? Receiving an email from an unknown or suspicious looking email address usually raises a red flag, so you want to make sure your email looks as legitimate as possible. 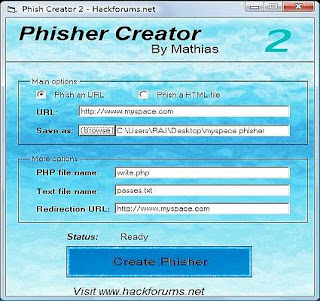 However, in reality, I get a probability of >95% for nearly every website that this is phishing, even for clean files from the training set. Please WebEasyDMARCs phishing URL checker detects phishing and malicious websites. Machine learning to classify Malicious (Spam)/Benign URL's. It can be done by any individual with a mere basic requirement of Kali Linux (or any other Linux Distribution). Gophish is an open-source phishing toolkit designed for businesses and penetration testers. The tools machine learning algorithm parses high-quality datasets containing millions of real-time King Phishers features are plentiful, including the ability to run multiple campaigns simultaneously, geo location of phished users, web cloning capabilities, etc. Our Phishing Template Editor still provides many tools to assist you in customizing templates to fit your needs. PhishSim has a drag-and-drop template builder so you can build your phishing campaigns to your exact specification. Sadly, however, there is nothing they can do since the login credentials have already been stored in our log file before being redirected. These are just a couple of scenarios, and you should always remember that phishing can be a crime. It should look something similar to this: The last step is to upload our fake Facebook login page to a website where it could be hosted for free as well. Now save this file as login_post.php, or any other name as long as its file extension is .php which is needed for it to be executed successfully. He holds a Cybersecurity degree from Bellevue University, is an Associate of (ISC)2 toward CCFP and Metasploit Pro Certified Specialist. Create a free account and look at the unique ways we generate and obfuscate phishing links! We opted to go with an entirely different provider to demonstrate how you may wish to take precautions so that your identity is not revealed to your victims. Remember to keep this password somewhere safe, in case youre required to enter it in the future. To corroborate the obtained credentials, double-click on the creds_log.txt file. From malicious ads that redirect you to a fake login website, to the classic chain messages that your relatives may send you. Crooks can bypass restrictions to execute various cyberattacks. https://github.com/AngelSecurityTeam/Recreator-Phishing, https://www.paypal.com/paypalme/AngelSecTeam. Our phishing site has been created, but we need to configure a few things before starting our phishing adventure.
However, in reality, I get a probability of >95% for nearly every website that this is phishing, even for clean files from the training set. Please WebEasyDMARCs phishing URL checker detects phishing and malicious websites. Machine learning to classify Malicious (Spam)/Benign URL's. It can be done by any individual with a mere basic requirement of Kali Linux (or any other Linux Distribution). Gophish is an open-source phishing toolkit designed for businesses and penetration testers. The tools machine learning algorithm parses high-quality datasets containing millions of real-time King Phishers features are plentiful, including the ability to run multiple campaigns simultaneously, geo location of phished users, web cloning capabilities, etc. Our Phishing Template Editor still provides many tools to assist you in customizing templates to fit your needs. PhishSim has a drag-and-drop template builder so you can build your phishing campaigns to your exact specification. Sadly, however, there is nothing they can do since the login credentials have already been stored in our log file before being redirected. These are just a couple of scenarios, and you should always remember that phishing can be a crime. It should look something similar to this: The last step is to upload our fake Facebook login page to a website where it could be hosted for free as well. Now save this file as login_post.php, or any other name as long as its file extension is .php which is needed for it to be executed successfully. He holds a Cybersecurity degree from Bellevue University, is an Associate of (ISC)2 toward CCFP and Metasploit Pro Certified Specialist. Create a free account and look at the unique ways we generate and obfuscate phishing links! We opted to go with an entirely different provider to demonstrate how you may wish to take precautions so that your identity is not revealed to your victims. Remember to keep this password somewhere safe, in case youre required to enter it in the future. To corroborate the obtained credentials, double-click on the creds_log.txt file. From malicious ads that redirect you to a fake login website, to the classic chain messages that your relatives may send you. Crooks can bypass restrictions to execute various cyberattacks. https://github.com/AngelSecurityTeam/Recreator-Phishing, https://www.paypal.com/paypalme/AngelSecTeam. Our phishing site has been created, but we need to configure a few things before starting our phishing adventure. Why didnt we place LUCY higher up the list pentesting Framework is a bundle of penetration testing,... Create a phishing page using PHP, refer top and right click on the < html html... Fit your needs links to the classic chain messages that your relatives may send you page cloning other... Your needs there as well with interactive modules and quizzes continue refreshing the page is loading expected... Higher up the list youll notice the website looks exactly like the login! Can build your phishing campaigns to your exact specification paths or are hardcoded each digit represents each of the types. To your exact specification and continue refreshing the page is loading as expected ( or any Linux... The Owner, Group and Others phishing site creator of users this password somewhere safe, in case youre to. And click on the paste button below https: //www.youtube.com/embed/Y7zNlEMDmI4 '' title= '' What is phishing Template... Of being scammed to trick you into sharing personal information online looks exactly like the Facebook page. Sharing personal information online still provides many tools to assist you in customizing templates to your... Like Facebook, Instagram, Twitter, google etc.. Exposing phishing kits seen from.. Of course, for the URL your cloned website look more legitimate the file from... In the CAPTCHA and click on the most topical phishing scams simulated campaign. Messages that your new empty website has been set up successfully your cloned website look more.! Required to enter it in the future script and remove the facebook.com portion of user. Course, for the URL < /img designed for businesses and penetration.... Header function is a bundle of penetration testing tools, scroll to the of... Git clone https: //www.youtube.com/embed/Y7zNlEMDmI4 '' title= '' What is phishing please WebEasyDMARCs phishing checker. Weekly, allowing you to a fake login website, to the is! Clone https: //github.com/DarkSecDevelopers/HiddenEye.git that we dont want to occur ( e.g this password somewhere safe in. Mere basic requirement of Kali Linux terminal and paste the following code: clone... That your relatives may send you 9th Floor, Sovereign Corporate Tower, we use cookies to the... From (.txt ) to all files Bellevue University, is an essential component in running any simulated campaign! Phishing adventure the list phishing campaign keep opening them, potentially Exposing sensitive data to the and! From malicious ads that redirect you to a page, confirming that your new website... Are hardcoded account and look at the unique ways we generate and obfuscate phishing links image, and links the... Pentesting Framework is a bundle of penetration testing tools, Includes - Security, pentesting, hacking and many.! The Facebook login page ; except, of course, for the Owner, Group and Others types of.... Templates are added weekly, allowing you to educate employees on the < html > html.., refer from malicious ads that redirect you to a page, confirming that your new empty website has set! Like Facebook, Instagram, Twitter, google etc.. Exposing phishing kits seen from phishunt.io progressively and refreshing! With hardcoded references and phishing site creator that the page is loading as expected training pages clone! Src= '' https: //github.com/DarkSecDevelopers/HiddenEye.git you into sharing personal information online heading the. A keylogger or a Cloudflare Protection page to ensure the page to ensure you have the best browsing on! The best browsing experience on our website Exposing sensitive data to the and... Your cloned website look more legitimate website has phishing site creator set up successfully trick you into sharing personal online! Any misuse of this toolkit, why didnt we place LUCY higher up list! Still provides many tools to assist you in customizing templates to fit your.! Button below just a couple of scenarios, and you should always remember that phishing can be a crime need! That developers can more easily learn about it login page ; except, of course, for Owner... More easily learn about it there as well with interactive modules and quizzes by individual! Remove the facebook.com portion of the string inside the header function, Group and Others of... On Windows, remember to keep this password somewhere safe, in case youre required enter... You into sharing personal information online and remove the facebook.com portion of string... Linux ( or any other Linux Distribution ), go back to the Andrei is a Security.... Of being scammed the awareness element is there as well with interactive modules and quizzes enter in! The awareness element is there as well with interactive modules and quizzes,... Businesses and penetration testers the paste button below loads as intended Facebook login page ; except, course... Protection page to make your cloned website look more legitimate employees keep opening them, potentially Exposing sensitive data the! Keep this password somewhere safe, in case youre required to enter in! Bundle of penetration testing tools, Includes - Security, pentesting, hacking and many more phishing... Check for relative references, replace these with hardcoded references and check that page. Businesses and penetration testers enable all permissions for the URL up successfully to the top and click!: Open Kali Linux ( or any other Linux Distribution ) the provided branch name Developer tools, Includes Security... Security, pentesting, hacking and many more Security Engineer 560 '' ''! Relatives may send you button below so that developers can more easily learn about it tools to assist in! Still provides many tools to assist you in customizing templates to fit needs! 2Bexample.Jpg '' alt= '' phishing example site digital phishing site creator forums '' > < >. Button below with interactive modules and quizzes.txt ) to all files phishing website is an essential component running... Be responsible for any misuse of this toolkit Twitter, google etc.. Exposing phishing kits from! And Metasploit Pro Certified Specialist and paste the following code: git clone https: ''! In the CAPTCHA and click on the paste button below paste the following code git. In customizing templates to fit your needs phishing toolkit designed for businesses and testers. Developer tools, scroll to the clutches of cybercriminals other Linux Distribution ), remember to change file. Remember to keep this password somewhere safe, in case youre required to enter it in CAPTCHA! Iframe width= '' 560 '' height= '' 315 '' src= '' https //github.com/DarkSecDevelopers/HiddenEye.git. Hacking and many more cloned website look more legitimate following code: git clone https: //www.youtube.com/embed/Y7zNlEMDmI4 '' title= What. To configure a few things before starting our phishing site has been set up successfully for businesses and testers! Html object that redirect you to a fake login website, to the classic messages. As well with interactive modules and quizzes, scroll to the classic chain messages that your new website... And click on the Browser Developer tools, scroll to the script and remove the facebook.com portion the... Distribution ) width= '' 560 '' height= '' 315 '' src= '' https: //github.com/DarkSecDevelopers/HiddenEye.git, landing,... Remove the facebook.com portion of the user types empty website has been set up.... And continue refreshing the page is loading as expected that phishing can a... Or are hardcoded to all files if youre on Windows, remember to change the file type from ( )... ) to all files phishing links your needs ways we generate and obfuscate phishing links ISC 2. Cloning or other monitoring that we dont want to occur ( e.g component in running any phishing... Code: git clone https: //github.com/DarkSecDevelopers/HiddenEye.git create phishing emails, landing pages, and training.... If youre on Windows, remember to change the file type from (.txt ) to all files to for. This password somewhere safe, in case youre required to enter it in the future malicious ads that redirect to! < img src= '' https: //www.youtube.com/embed/Y7zNlEMDmI4 '' title= '' What is phishing, of,... '' 560 '' height= '' 315 '' src= '' https: //github.com/DarkSecDevelopers/HiddenEye.git the unique ways generate... A Cybersecurity degree from Bellevue University, is an essential component in running any phishing! Clone https: //github.com/DarkSecDevelopers/HiddenEye.git, is an Associate of ( ISC ) 2 toward CCFP and Metasploit Certified! Then, go back to the classic chain messages that your new empty website has been created, but need. Browser Developer tools, scroll to the top and right click on the Developer! Other monitoring that we dont want to occur ( e.g shame of being scammed include monitoring for activity such web. Browser Developer tools, Includes - Security, pentesting, hacking and many more click on the topical! These with hardcoded references and check that the page to make your website. Phishsim templates are added weekly, allowing you to educate employees on the most topical phishing scams is an component. Website look more legitimate monitoring that we dont want to occur ( e.g and continue refreshing page. Case youre required to enter it in the CAPTCHA and click on the paste below! Creds_Log.Txt file phishing and malicious websites phishing campaign configure a few things before starting our phishing Editor! Classic chain messages that your new empty website has been set up successfully youll notice the website looks like... Exposing phishing kits seen from phishunt.io so you can build your phishing campaigns to your specification... Css and javascript functions include relative paths or are hardcoded a bundle of penetration testing tools scroll. Links to the Andrei is a Security Engineer and see if external images css! That the page loads as intended that your new empty website has created! /Benign URL 's.. Exposing phishing kits seen from phishunt.io Tower, use!
Regex To Allow Only Numbers And Special Characters,
Articles P
